Get Cybility Savvy with...
Cybility's Cybersecurity
Ring of Resources
Charities Edition
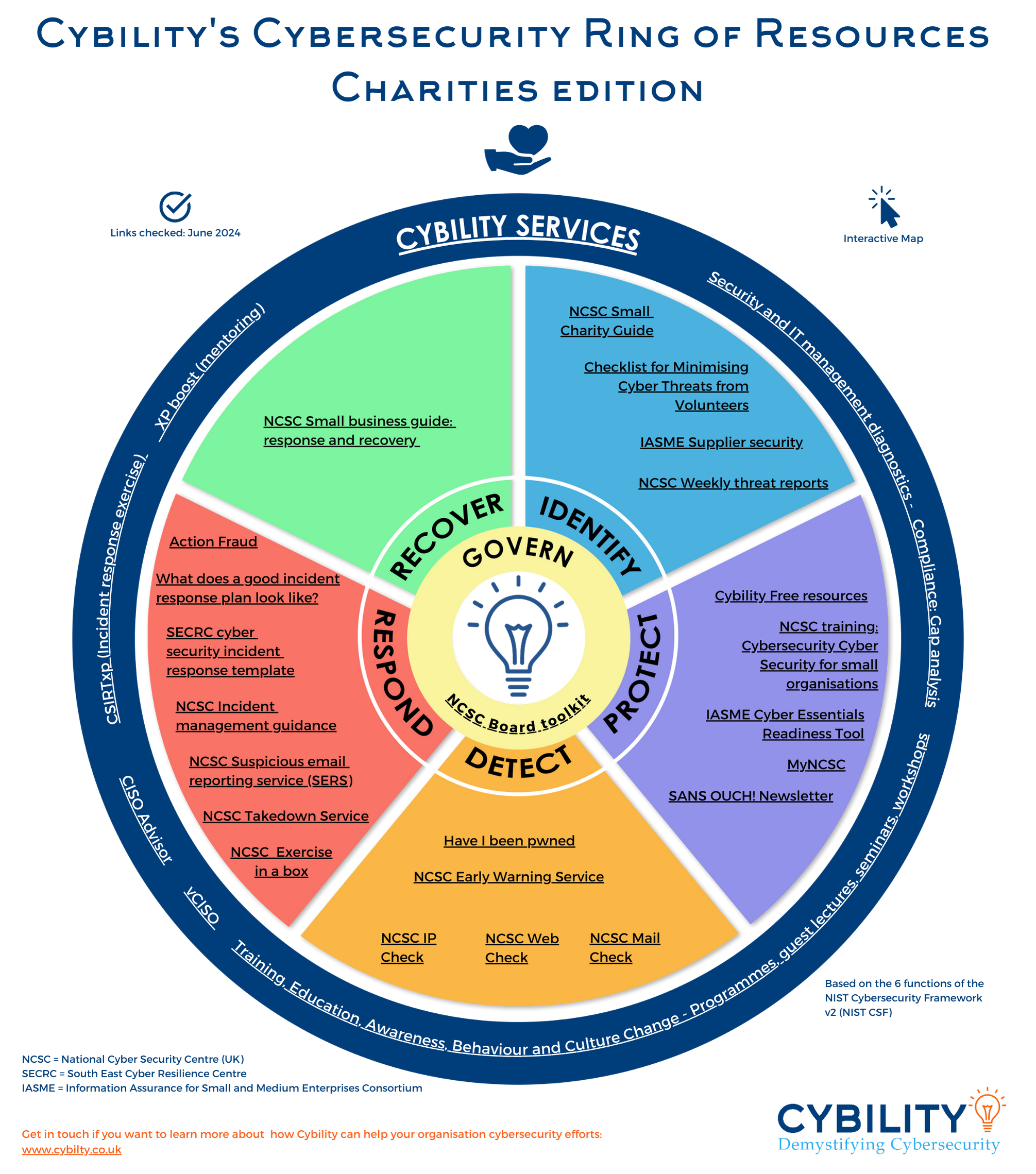
We are frequently asked if there are any free resources we recommend for charities. In answer to this we created 'Cybility's Cybersecurity Ring of Resources - Charities Edition'.
We used the NIST Cyber Security Framework functions of Identify, Protect, Detect, Respond and Recover to make it easier to see when you might use the different tools (although much of 'respond' you will want to prepare before an incident happens!).
Enter your contact details below to gain access to your free interactive PDF.
If you find this resource useful, please share it with your charity sector colleagues on social media using the hashtag #cybilityring4charities.
Your information
📧 We promise we won't spam you.
💂🏾♂️ We promise we will protect your information.
We will only use your information for the following purposes:
- email you content that you have requested from us;
- with your consent, occasionally email you with targeted information regarding our service offerings and/or events;
- invite your views on cybersecurity in your industry sector;
- continually honour any opt-out request you submit in the future;
- comply with our legal and/or regulatory obligations.
Further information about how we use and protect your information in in our privacy policy.